Content
- GST 2.0 could undermine dietary health
- India–China: the need for a border settlement
- How does two-factor authentication (2FA) work?
- At least 19 killed in Nepal protests; Sharma Oli govt. revokes social media ban
- Vembanad Lake crisis
GST 2.0 could undermine dietary health
Why in News
- From 22 September 2025, India will implement GST 2.0 with a simplified structure:
- Two main slabs: 5% and 18%.
- A special 40% “sinful/ultra-luxury” bracket.
- Many everyday foods (pizza bread, confectionery, chocolates, jams, jellies) will shift to lower tax slabs (5% or zero).
- Aerated and sugar-based beverages will move to the 40% bracket.
- Concern: While simplifying GST, these changes may undermine public health goals by making unhealthy foods more affordable.
Relevance : GS III (Economy – Tax Policy, Public Health, Nutrition Security, Non-Communicable Disease Prevention).
From Basics
- GST Basics:
- Introduced in 2017 → “One Nation, One Tax” indirect tax reform.
- Prior slabs: 5%, 12%, 18%, 28% (+ cess).
- GST 2.0 → rationalised to 5% and 18%, with 40% sin tax for harmful/luxury goods.
- Non-Communicable Diseases (NCDs) in India:
- Account for ~65% of deaths (WHO, MoHFW data).
- Diet-related risk factors: high sugar, salt, fat consumption → obesity, diabetes, hypertension, cardiovascular disease.
- Front-of-Pack Labelling (FOPL):
- Proposed by FSSAI in 2022, still not finalised.
- Supreme Court (July 2025): ordered FSSAI to finalise norms within 3 months.
- Debate: Health Star Rating vs “High-in” Warning Labels.
- WHO-SEARO’s Nutrient Profile Model (NPM): recommends category-based cut-offs for sugar, sodium, fats.
- Advertising Rules (Current):
- HFSS foods banned near schools (FSSAI 2020).
- CCPA 2022 → restrictions on misleading ads.
- ASCI 2024 → expanded disclosure norms.
- Still no comprehensive HFSS advertising regulation comparable to Chile or UK.
Comprehensive Overview
Positive Aspects of GST 2.0
- Simplification of structure → reduces compliance burden.
- 40% sin tax on aerated drinks → aligns with global best practices.
- Studies (Asia, Africa) show 2.5–19% consumption decline after sugar taxes.
- Can nudge reformulation of sugary drinks if linked with labelling and ad restrictions.
Public Health Concerns
- Unhealthy foods becoming cheaper:
- Pizza bread (including maida-based) exempted.
- Chocolates, jams, confectionery moved to 5%.
- Mismatch in taxation: sugary beverages penalised, but sugary foods incentivised.
- Risk of substitution: adolescents may shift from taxed beverages to untaxed sugary snacks.
Weakness in Regulatory Ecosystem
- Food Labelling Gaps:
- Without mandatory FOPL, consumers can’t differentiate healthy vs unhealthy products.
- “Per serving” labels misleading → need per 100g/ml thresholds.
- Advertising Gaps:
- No restriction on HFSS ads across TV, social media, print.
- Chile’s model (ban on child-directed advertising of “high in” foods) more effective.
Policy Corrections Needed
- Link GST with FOPL:
- Products breaching “high in” thresholds → taxed 18% or higher.
- Compliant products → taxed 5% or lower.
- Mandatory Warning Labels:
- Adopt WHO-SEARO or ICMR-NIN thresholds.
- Apply per-quantity norms to avoid loopholes.
- Stronger Ad Regulation:
- Ban ads for “high in” products to children.
- Restrict ad slots during peak child-viewing hours.
- Use of Sin-Tax Revenues:
- Redirect to NCD prevention, labelling enforcement, reformulation incentives.
Long-Term Implications
- If uncorrected, GST 2.0 could increase NCD burden, straining healthcare.
- Integrated approach needed: Tax Policy + Labelling + Advertising Regulation.
- India can set a global example by aligning fiscal and health policies.
India-China: the need for a border settlement
Why in News
- On 19 August 2025, India and China held the 24th round of Special Representatives (SR) talks on the boundary issue.
- Talks resumed after a five-year gap (2019–2024) due to the 2020 border crisis.
- Both sides reiterated commitment to the 2005 “Political Parameters and Guiding Principles” agreement as the framework for settlement.
- Agreed to focus on:
- Early harvest settlement of the Sikkim–Tibet boundary.
- New border management mechanisms to prevent 2020-like incidents.
Relevance : GS II (International Relations – Boundary Dispute, Security, Diplomacy, Strategic Affairs).
From Basics
- Historical Context:
- Boundary dispute dates back to colonial demarcations → McMahon Line (Arunachal Pradesh) and Aksai Chin (Ladakh).
- 1962 war → unresolved borders, mistrust.
- 1979 Vajpayee’s visit to China → beginning of normalization.
- Vajpayee’s Role:
- 1998 nuclear tests soured ties, but reconciliation followed.
- 2003: Vajpayee’s visit → Special Representatives (SR) mechanism set up (NSA-level talks).
- Aim: political, not purely technical, resolution.
- 2005 Political Parameters Agreement:
- Settlement to consider strategic interests and settled populations.
- Suggested swap deal:
- China keeps Aksai Chin (strategically vital for it).
- India retains Arunachal Pradesh (populated, culturally tied to India).
- Articles:
- Art. IV – “mutual and equal security”.
- Art. VII – “interests of settled populations” to be protected.
- Subsequent Developments:
- 2007: China reasserted claim on Tawang (Arunachal Pradesh) despite Article VII.
- 2013: Both sides reached 18-point consensus (per Menon & Chinese Ambassador Wei Wei).
- Doklam crisis (2017) → revealed partial agreements (Sikkim-Tibet watershed alignment).
- 2020 Galwan crisis → major breakdown of trust, collapse of existing CBMs.
Comprehensive Overview
Strategic Significance of Settlement
- For India:
- Secure borders → reduce military costs of LAC deployment.
- Focus on core strategic challenges (Indian Ocean, Pakistan).
- Normalize relations with China → boost trade & diplomacy.
- For China:
- Stable border allows focus on Taiwan, South China Sea.
- Secures Aksai Chin (vital for Xinjiang–Tibet connectivity).
- Prevents India–U.S. alignment from hardening further.
Key Roadblocks
- Tawang Issue: China insists India concede Tawang, despite India’s settled populations argument.
- Mistrust: 2020 Galwan clash → CBMs (1993, 1996, 2005, 2013) undermined.
- Domestic Politics: Both leaderships risk being seen as compromising on sovereignty.
- Geopolitical Factors: U.S.–China rivalry makes Beijing cautious about India’s growing alignment with Quad.
Present Status (2025)
- 24th SR talks revived the 2005 framework.
- Agreement to:
- Prioritize Sikkim–Tibet boundary finalization (low-hanging fruit).
- Devise new border management mechanisms beyond failed 1996/2005 CBMs.
- Military deployments remain high → both sides paying heavy economic and strategic costs.
The Way Forward
- Political Will Required: A deal exists in principle since 2005–2013; execution stalled by lack of leadership consensus.
- Incremental Approach: Start with Sikkim-Tibet “early harvest”, expand to Ladakh–Arunachal.
- Revived CBMs: Joint patrolling, hotlines, no-weapons protocols must be reworked.
- Strategic Compromise: Both sides must accept “as is, where is” logic — Aksai Chin with China, Arunachal with India.
Key Takeaways
- The 2005 Political Parameters Agreement remains the only negotiated document on India–China boundary.
- Settlement is technically feasible but blocked by political reluctance and trust deficit.
- Without resolution, both countries bear escalating military and economic costs at the LAC.
- A breakthrough requires top-level political push, as Vajpayee once attempted in 2003.
How does two-factor authentication (2FA) work?
Why in News
- Growing cyber threats have exposed the limitations of password-only authentication.
- Increasing adoption of Two-Factor Authentication (2FA) by services like Google, Facebook, banks, and government portals.
- Popular implementations: Google Authenticator, Authy, Microsoft Authenticator, YubiKey.
Relevance : GS III (Internal Security – Cybersecurity, Authentication Technologies, Digital Governance).
From Basics
- Passwords Alone Are Not Enough:
- Vulnerable to theft, phishing, brute-force attacks.
- If compromised, attackers gain full access without user awareness.
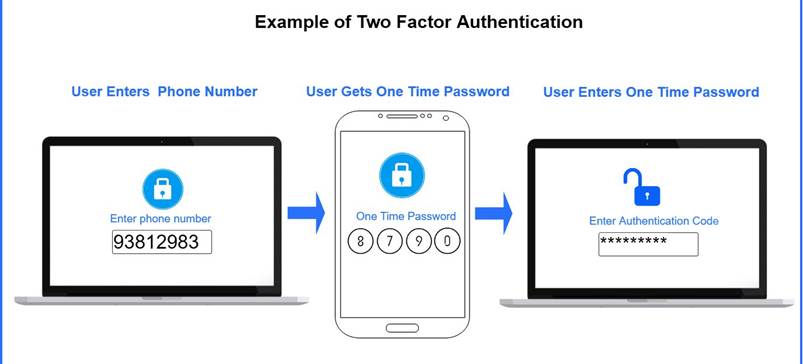
- What is 2FA?
- Authentication via two factors:
- Something you know → Password.
- Something you have → Authenticator app/device.
- Example: Even with a stolen password, attacker also needs access to your phone.
- Authentication via two factors:
- One-Time Passwords (OTPs):
- Short numeric codes valid for a few seconds.
- Prevents reuse → intercepted code becomes useless.
- Time-based One-Time Passwords (TOTP):
- Defined by open standard (RFC 6238).
- Uses secret key + current time to generate 6-digit code every 30 seconds.
- Widely supported across platforms → interoperability.
- How TOTP Works:
- Service shares a secret key (via QR code).
- Both server and authenticator app calculate code using:
- Shared secret.
- Time counter (increments every 30 seconds).
- Cryptographic hash function.
- Result → 6-digit code displayed on app, verified by server.
- Hash Functions:
- Convert variable-length input → fixed-length output (e.g., SHA-256 → 256-bit).
- Properties: one-way, collision-resistant, sensitive to small input changes.
- HMAC (Hash-based Message Authentication Code):
- Combines secret key with message using hash function securely.
- Provides integrity + authenticity.
- Formula involves XOR mixing with pads (inner & outer).
- XOR in Cryptography:
- Logical operation: outputs 1 if inputs differ, 0 if same.
- Reversible → crucial in encryption and authentication schemes.
Comprehensive Overview
Security Strengths
- Layered defence: requires both password + device.
- Time sensitivity: codes valid only for 30 seconds.
- Unpredictability: without secret key, output cannot be derived.
- Compatibility: TOTP standard ensures same method across apps.
Limitations & Risks
- Device Loss: if phone is lost, access recovery can be difficult.
- Phishing Attacks: real-time phishing kits can capture OTPs.
- Man-in-the-Middle Attacks: attacker intercepts OTP during login.
- User Inconvenience: setup and backup keys often neglected.
Alternatives & Variants
- HOTP (HMAC-based OTP) → counter instead of time, less common.
- Push-based 2FA → approval via notification, not manual code.
- Hardware Tokens (e.g., YubiKeys) → physical device generates secure codes.
- Biometrics → fingerprint, face, or iris as second factor.
Broader Implications
- Cybersecurity Policy: governments, banks, and enterprises encourage 2FA adoption.
- Digital India/UIDAI Context: Aadhaar-enabled authentication also uses multi-factor.
- Global Cyber Norms: alignment with zero-trust security architecture.
Key Takeaways
- 2FA and TOTP provide significantly higher protection than passwords alone.
- Based on cryptographic principles (hash, HMAC, XOR) and time-based counters.
- Adoption challenges remain (phishing, user convenience), but it is a necessary global cybersecurity standard.
At least 19 killed in Nepal protests; Sharma Oli govt. revokes social media ban
Why in News
- Nepal witnessed unprecedented protests led mainly by Gen Z youth against the government’s ban on social media platforms.
- Trigger: Government ordered registration of digital platforms, curbs on “objectionable posts”, and blocked apps like TikTok, Viber, and Bigo Live.
- Protests escalated into violent clashes near Parliament in Kathmandu; 19 killed, many injured.
- The movement reflects deeper anger at corruption, political dynasties, and lack of accountability.
Relevance : GS II (International Relations – India–Nepal, Democracy, Governance, Civil Liberties, Political Movements).

From Basics
- Nepal’s Democracy:
- Transitioned from monarchy → democracy (2008).
- Federal democratic republic with frequent political instability.
- Social Media in Nepal:
- Primary platform for youth expression, activism, and dissent.
- Used to highlight corruption, nepotism (“Nepo Babies”), and demand accountability.
- Especially critical for Gen Z (large share of Nepal’s population is below 30).
- Legal Context:
- Government claimed regulation was needed to curb misinformation and harmful content.
- Critics: Seen as muzzling dissent, shrinking civic space, undermining free speech.
Comprehensive Overview
Political Context
- Youth anger directed at entrenched political class (Pushpa Kamal Dahal ‘Prachanda’, Sher Bahadur Deuba, K.P. Sharma Oli).
- Allegations: misuse of power, corruption in aid, infrastructure contracts, and wealth accumulation by political elites.
- Rotational politics among same leaders since 2006 peace process → perception of stagnation.
Social Dimension
- Gen Z frustration: lack of jobs, poor governance, and corruption.
- Social media as only outlet for voice → crackdown triggered massive backlash.
- “Nepo Babies” trend: exposing privileges of children of leaders.
Legal & Governance Issues
- Government rationale: curb fake news, hate speech, and “objectionable posts”.
- Reality: disproportionate restrictions → violation of free expression, association, and privacy.
- Opposition parties & rights groups: called it an authoritarian overreach.
Economic Concerns
- Nepal’s weak economy, high youth unemployment, and migration reliance (remittances).
- Social media bans hurt small businesses, digital creators, and diaspora communication.
Geopolitical Angle
- Nepal caught between India and China’s influence.
- Social media restrictions could push Nepal closer to China-style digital authoritarianism.
- Impacts Nepal’s democratic credentials regionally and globally.
Broader Implications
- Ban symbolises clash between youth aspirations vs. entrenched elite politics.
- Raises questions about state control over digital spaces in fragile democracies.
- May fuel long-term distrust in institutions and radicalisation of youth movements.
Key Takeaways
- Social media ban is only the trigger → the real issue is youth disillusionment with corruption, dynastic politics, and lack of accountability.
- Nepal faces a democratic backsliding risk if bans and curbs on free expression continue.
- Stability requires reforms: youth participation in governance, anti-corruption measures, transparency, and balancing digital regulation with rights.
Vembanad Lake crisis
Why in News
- Vembanad Lake, Kerala’s largest wetland and a Ramsar site, faces severe ecological degradation.
- Unchecked tourism (luxury houseboats), encroachment, sewage, and reclamation threaten its survival.
- A CWRDM report shows boat numbers have exceeded carrying capacity → pushing the ecosystem to collapse.
Relevance : GS III (Environment – Wetlands, Ramsar Sites, Ecological Degradation, Sustainable Tourism, Climate Resilience).

From Basics
- Location: Spans Alappuzha, Kottayam, Ernakulam districts in Kerala.
- Ecological importance:
- Largest Ramsar site in Kerala.
- Regulates floods, nourishes paddy fields (Kuttanad region – “Rice Bowl of Kerala”), sustains fisheries.
- Habitat for mangroves, migratory birds, and aquatic life.
- Socio-economic role:
- Supports fishing communities.
- Central to Kerala’s backwater tourism (houseboats, shikaras).
Comprehensive Overview
Tourism Pressure
- Traditional kettuvalloms turned into luxury floating resorts.
- Safe capacity: 461 houseboats → Actual: 954 + 241 shikaras + 404 motorboats + 1,625 country boats.
- Impact: Sewage discharge, diesel pollution, boat congestion → erosion, breeding ground destruction.
Water Pollution
- Coliform levels near Punnamada: 8,000 → lake turning into “floating septic tank”.
- Sewage treatment infrastructure largely idle.
- Churning wakes disturb sediments → ecological imbalance.
Impact on Communities
- Fisherfolk displaced from traditional fishing grounds.
- Declining fish catch → loss of livelihoods.
- Increased vulnerability to floods and droughts.
Wetland Degradation
- Area shrinkage: 130.68 sq. km (1967) → 3.29 sq. km (2011).
- Ongoing annual reduction: ~0.3 sq. km.
- Encroachments: illegal resorts, land reclamation, high-rises.
- Example: 2019 Maradu flats demolition → exposed 26,000+ violations.
Governance & Policy Issues
- Tourism-politics nexus → reluctance to regulate.
- Judicial interventions (SC orders demolitions) address visible violations, but invisible pressures (houseboat sewage, congestion) remain unchecked.
- Lack of integrated wetland management plan.
Proposed Solutions
- Ban non-local boats, regulate carrying capacity.
- Waste treatment mandatory at hubs.
- Declare Vembanad a fish sanctuary (as proposed by KSSP).
- Promote eco-tourism, restrict entry into sensitive zones.
- Balance tourism revenue with ecological sustainability.
Broader Significance
- Environmental: Wetland collapse → loss of biodiversity, flood regulation capacity.
- Economic: Threat to fisheries, paddy cultivation, and long-term tourism viability.
- Social: Marginalisation of local communities, cultural displacement.
- Climate Change Context: Kerala’s recurrent floods make Vembanad’s survival critical for resilience.