Why in News
- Growing cyber threats have exposed the limitations of password-only authentication.
- Increasing adoption of Two-Factor Authentication (2FA) by services like Google, Facebook, banks, and government portals.
- Popular implementations: Google Authenticator, Authy, Microsoft Authenticator, YubiKey.
Relevance : GS III (Internal Security – Cybersecurity, Authentication Technologies, Digital Governance).
From Basics
- Passwords Alone Are Not Enough:
- Vulnerable to theft, phishing, brute-force attacks.
- If compromised, attackers gain full access without user awareness.
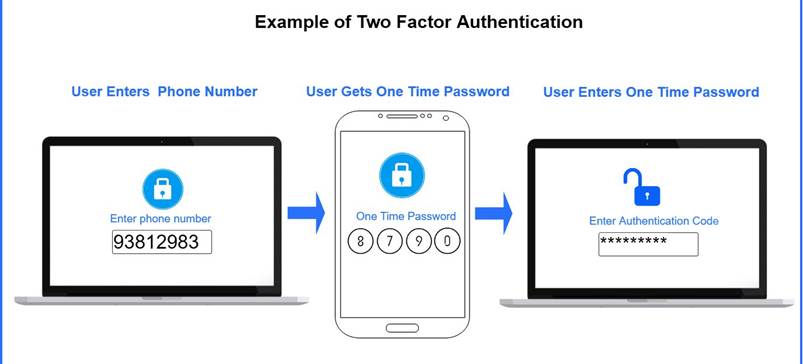
- What is 2FA?
- Authentication via two factors:
- Something you know → Password.
- Something you have → Authenticator app/device.
- Example: Even with a stolen password, attacker also needs access to your phone.
- Authentication via two factors:
- One-Time Passwords (OTPs):
- Short numeric codes valid for a few seconds.
- Prevents reuse → intercepted code becomes useless.
- Time-based One-Time Passwords (TOTP):
- Defined by open standard (RFC 6238).
- Uses secret key + current time to generate 6-digit code every 30 seconds.
- Widely supported across platforms → interoperability.
- How TOTP Works:
- Service shares a secret key (via QR code).
- Both server and authenticator app calculate code using:
- Shared secret.
- Time counter (increments every 30 seconds).
- Cryptographic hash function.
- Result → 6-digit code displayed on app, verified by server.
- Hash Functions:
- Convert variable-length input → fixed-length output (e.g., SHA-256 → 256-bit).
- Properties: one-way, collision-resistant, sensitive to small input changes.
- HMAC (Hash-based Message Authentication Code):
- Combines secret key with message using hash function securely.
- Provides integrity + authenticity.
- Formula involves XOR mixing with pads (inner & outer).
- XOR in Cryptography:
- Logical operation: outputs 1 if inputs differ, 0 if same.
- Reversible → crucial in encryption and authentication schemes.
Comprehensive Overview
Security Strengths
- Layered defence: requires both password + device.
- Time sensitivity: codes valid only for 30 seconds.
- Unpredictability: without secret key, output cannot be derived.
- Compatibility: TOTP standard ensures same method across apps.
Limitations & Risks
- Device Loss: if phone is lost, access recovery can be difficult.
- Phishing Attacks: real-time phishing kits can capture OTPs.
- Man-in-the-Middle Attacks: attacker intercepts OTP during login.
- User Inconvenience: setup and backup keys often neglected.
Alternatives & Variants
- HOTP (HMAC-based OTP) → counter instead of time, less common.
- Push-based 2FA → approval via notification, not manual code.
- Hardware Tokens (e.g., YubiKeys) → physical device generates secure codes.
- Biometrics → fingerprint, face, or iris as second factor.
Broader Implications
- Cybersecurity Policy: governments, banks, and enterprises encourage 2FA adoption.
- Digital India/UIDAI Context: Aadhaar-enabled authentication also uses multi-factor.
- Global Cyber Norms: alignment with zero-trust security architecture.
Key Takeaways
- 2FA and TOTP provide significantly higher protection than passwords alone.
- Based on cryptographic principles (hash, HMAC, XOR) and time-based counters.
- Adoption challenges remain (phishing, user convenience), but it is a necessary global cybersecurity standard.